“RDP is a double-edged sword — it offers seamless remote access, but in the wrong hands, it’s a doorway for attackers. In this post, we trace every footprint RDP leaves in your event logs.”
🧠 RDP in Forensics
Remote Desktop Protocol (RDP) is one of the most common entry points in Windows environments — both for system administrators and malicious actors. Understanding the chain of RDP-related Event IDs allows defenders to reconstruct session activity, identify unauthorized access, and correlate logins, re-connections, and logoffs.
This blog post breaks down key RDP events and presents a timeline-style visualization of an RDP session lifecycle.
🔐 Successful Logon: The Forensic Breadcrumbs
When a valid RDP session is established, the following Event IDs are triggered:
| Event ID | Description | Log Source |
|---|---|---|
| 1149 | User authentication succeeded | RemoteConnectionManager |
| 4624 (Type 10/7) | Logon success | Security.evtx |
| 21, 22 | Shell start / session logon | LocalSessionManager |
🧠 Tip: Always correlate 1149 + 4624 for RDP logon confirmation. Type 10 (RemoteInteractive) is your smoking gun.
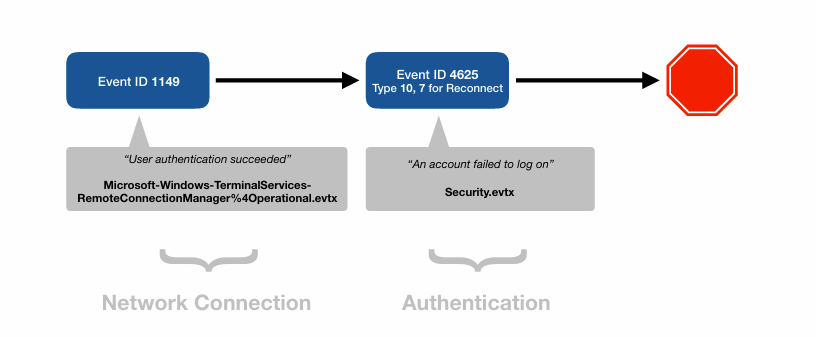
🚫 Unsuccessful Logon Attempts
Threat actors love brute-force RDP attacks. Track failed logon attempts using:
| Event ID | Description | Log Source |
|---|---|---|
| 1149 | Attempt made (still triggers!) | RemoteConnectionManager |
| 4625 | Account failed to log on | Security.evtx |
🔍 Watch for high-frequency 4625s followed by a successful 4624 — a sign of brute-force followed by success.
🔁 RDP Session Reconnects & Disconnects
Sessions can disconnect due to idle timeouts or network blips. Here’s how to track them:
| Event ID | What Happened | Source |
|---|---|---|
| 24, 40 | Session disconnected | LocalSessionManager |
| 4634 | Account logged off | Security.evtx |
| 4779 | Session disconnected from Window Station | Security.evtx |
| 25 | Session reconnection succeeded | LSM |
| 4778 | Session reconnected | Security.evtx |
📌 Reason codes in Event 40 can indicate whether the disconnect was manual, idle timeout, or network loss.
RDP Session Disconnect(Window Close)
RDP Session Disconnect(Purposefull Disconnect via start)
RDP Session Reconnect
—
🧾 RDP Logoff and Session End
The tail end of an RDP session logs final cleanup:
| Event ID | Meaning | Source |
|---|---|---|
| 23 | Logoff success | LSM |
| 4647 | User initiated logoff | Security.evtx |
| 9009 | Desktop Window Manager exited | System.evtx |
📎 Use Event 4647 to differentiate between user-initiated logoff vs. forced logoff. RDP Session Logoff —
🔧 Practical Use Case: Detecting Suspicious RDP Behavior
Let’s say you see the following sequence:
- Many
4625failures for useradmin - One successful
1149+4624(Type 10) - A quick
4634logoff
This could signal a brute-force attack followed by immediate reconnaissance and logoff.
Add contextual data like:
- Login time outside business hours
- Non-corporate IP address
- Unusual hostnames or session durations
🎨 RDP Timeline Visualization
Here’s a conceptual timeline:
1
2
3
4
5
6
7
[00:00] -> Event 1149: Auth attempt
[00:01] -> Event 4624: Success login (Type 10)
[00:02] -> Event 21/22: Shell/session initiated
[00:30] -> Event 40: Disconnected
[00:31] -> Event 25: Reconnected
[01:00] -> Event 4647: Logoff initiated
[01:00] -> Event 9009: DWM closed
🧭 Visual timelines like these help in threat hunting and post-incident investigations.
🔚 Final Thoughts
RDP event forensics isn’t just about detecting brute-force attacks — it’s about creating a narrative from logs. By correlating Event IDs across Security.evtx, System.evtx, and TerminalServices logs, you can reconstruct attacker behavior with high fidelity.


 Windows Forensics Tools
Windows Forensics Tools LNK File Forensics — Experimental Case Study
LNK File Forensics — Experimental Case Study Windows Artifacts
Windows Artifacts Windows 11 PCA Artifac
Windows 11 PCA Artifac