Resource Exhaustion Detection and Resolution (RADAR)
When investigating Windows systems, evidence of execution is gold. Artifacts like Prefetch, UserAssist, and ShimCache are well-known, but Windows quietly maintains another lesser-known record: RADAR (Resource Exhaustion Detection and Resolution).
First introduced in Windows Vista, RADAR continuously watches for processes consuming abnormal amounts of memory — often due to memory leaks. When a process crosses certain thresholds, RADAR records diagnostic data… and leaves a persistent registry trace that can confirm a program ran.
Registry Location
RADAR stores its findings in:
1
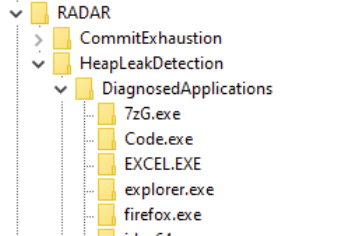
HKLM\Software\Microsoft\RADAR\HeapLeakDetection\DiagnosedApplications
Each subkey under DiagnosedApplications represents a flagged application, typically containing:
- Application name/path
- LastDetectionTime – a QWORD value in Windows FILETIME format
This tells us:
✅ The application ran
✅ RADAR flagged it for memory/resource issues
❌ But it does not tell us the exact execution time (only when RADAR detected the issue, which might be well after execution began).
Why It Matters in Forensics
1. A Lifeline on Server Systems
Servers often have Prefetch disabled for performance, removing one of our best-known execution artifacts. RADAR can still be present, making it an invaluable substitute.
2. Strengthens Corroboration
In DFIR, no single artifact is perfect. RADAR entries can back up findings from:
- Prefetch
- UserAssist
- ShimCache
- Event Logs
3. Timeline Context
LastDetectionTime acts as a lower bound for execution — the application must have been running at or before this time. It’s not precise, but it helps anchor the timeline.
⚠️ Important Limitations
It’s critical to understand what RADAR can and cannot tell you:
No Exact Execution Time
LastDetectionTimeis when RADAR detected abnormal memory use — not when the program started. The actual execution could be minutes, hours, or even days earlier.Selective Logging
RADAR only records processes it deems problematic. Well-behaved apps might never appear.- Context Needed
Presence of an entry suggests high resource usage, but this could be due to:- Software bugs
- Malware activity
- Legitimately heavy workloads
- Possible Absence in Some Cases
If the system didn’t hit the memory leak thresholds, there will be no record — even if the app ran.
Investigation Workflow
Step 1 – Registry Analysis
Open the registry hive (System’s SOFTWARE) in Registry Explorer (Eric Zimmerman) and navigate to:
1
HKLM\Software\Microsoft\RADAR\HeapLeakDetection\DiagnosedApplications
Export relevant subkeys for preservation.
Step 2 – Timestamp Conversion
Convert LastDetectionTime (FILETIME) to human-readable form. This will show the detection moment.
Step 3 – Correlate with Other Data
Cross-check with:
- Event Logs (System log, Event ID 2004 – Microsoft-Windows-Resource-Exhaustion-Detector)
- Prefetch (if available)
- Other execution artifacts
Event Log Correlation
When RADAR triggers, Event ID 2004 may appear in the System log, containing:
- Virtual memory status
- Top memory-consuming processes
- Detailed memory usage numbers
If this matches the RADAR registry entry, you have strong contextual evidence.
DFIR Best Practices
Include RADAR in Your Default Checks
Especially for servers or environments with missing traditional artifacts.- Document Precisely
Record:- Application name & path
LastDetectionTime(converted)- Supporting evidence
- Interpret Conservatively
Don’t claim RADAR shows the first run time — it only shows when RADAR noticed a problem while the app was running.
Conclusion
RADAR is a niche but valuable Windows execution artifact that’s often overlooked. It won’t replace Prefetch or UserAssist, but it can fill critical gaps — especially in server investigations.
By understanding its strengths (confirmation of execution, server applicability) and limitations (no exact start time, selective logging), investigators can use RADAR effectively to build stronger, more reliable forensic timelines.
Credit to researcher Harel Segev for the original deep dive into this artifact, showing once again how Windows still hides untapped forensic value.

 RADAR – An Obscure Execution Artifact
RADAR – An Obscure Execution Artifact
 Windows 11 PCA Artifac
Windows 11 PCA Artifac Windows Forensics Tools
Windows Forensics Tools LNK File Forensics — Experimental Case Study
LNK File Forensics — Experimental Case Study