Are Hardware KVMs the Next Big Blind Spot in Digital Forensics??
JetKVM: A $70 hardware KVM device that grants anyone full remote control of a computer-even when powered off or locked-via HDMI/USB emulation. No host software. No traditional forensic traces. Just pure hardware-level access.
https://github.com/jetkvm/kvm.git
https://www.kickstarter.com/projects/jetkvm/jetkvm
When Your Keyboard Is the Attacker
A Forensics Wake-Up Call!!
Invisible to EDR/XDR: Operates as a “Dell Monitor” or “Logitech Keyboard” in registry entries blend with legitimate hardware
Zero Memory Footprint: Leaves no process/network artifacts (unlike RDP/VNC)
The Forensic Blind Spot
- Registry Traces: Spoofed vendor IDs in
HKLM\SYSTEM\CurrentControlSet\Enum\USBmay be your only lead Network Red Flags:
No traceon the host machine as the device uses seperateLAN- Physical Evasion: Smaller than a keylogger and hides behind monitor cables
💡 Analyst Challenge:
How do you detect ?!
Our Observatiosn on Jet-KVM
After purchasing and testing JetKVM for forensic analysis, here’s what we discovered:
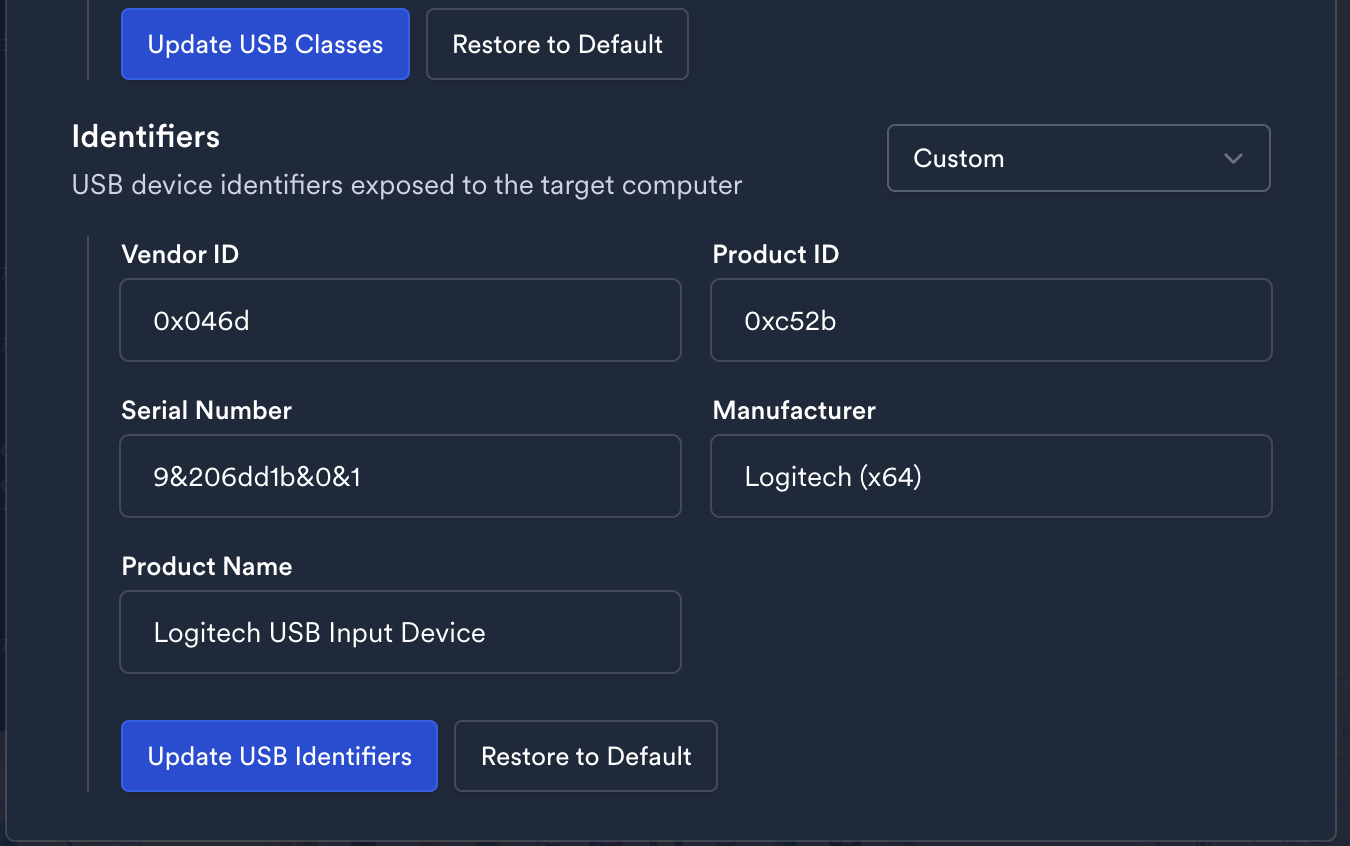
- Fully Customizable Device Identity
JetKVM appears to the system as just another external monitor or keyboard. Even more concerning, you can customize the device name, serial number, and other identifiers — so it could show up as “Dell Monitor,” “Logitech Keyboard,” or virtually anything you want in system registries and device managers.![Customizable Device Identity]()
Persistence Across Reboots and BIOS Access
Remote control via JetKVM persists even after a system reboot and is available during BIOS/UEFI setup. The device acts exactly like a local keyboard and monitor, allowing an attacker to change BIOS settings or boot order — no operating system needed.- EDID Cloning for Perfect Disguise
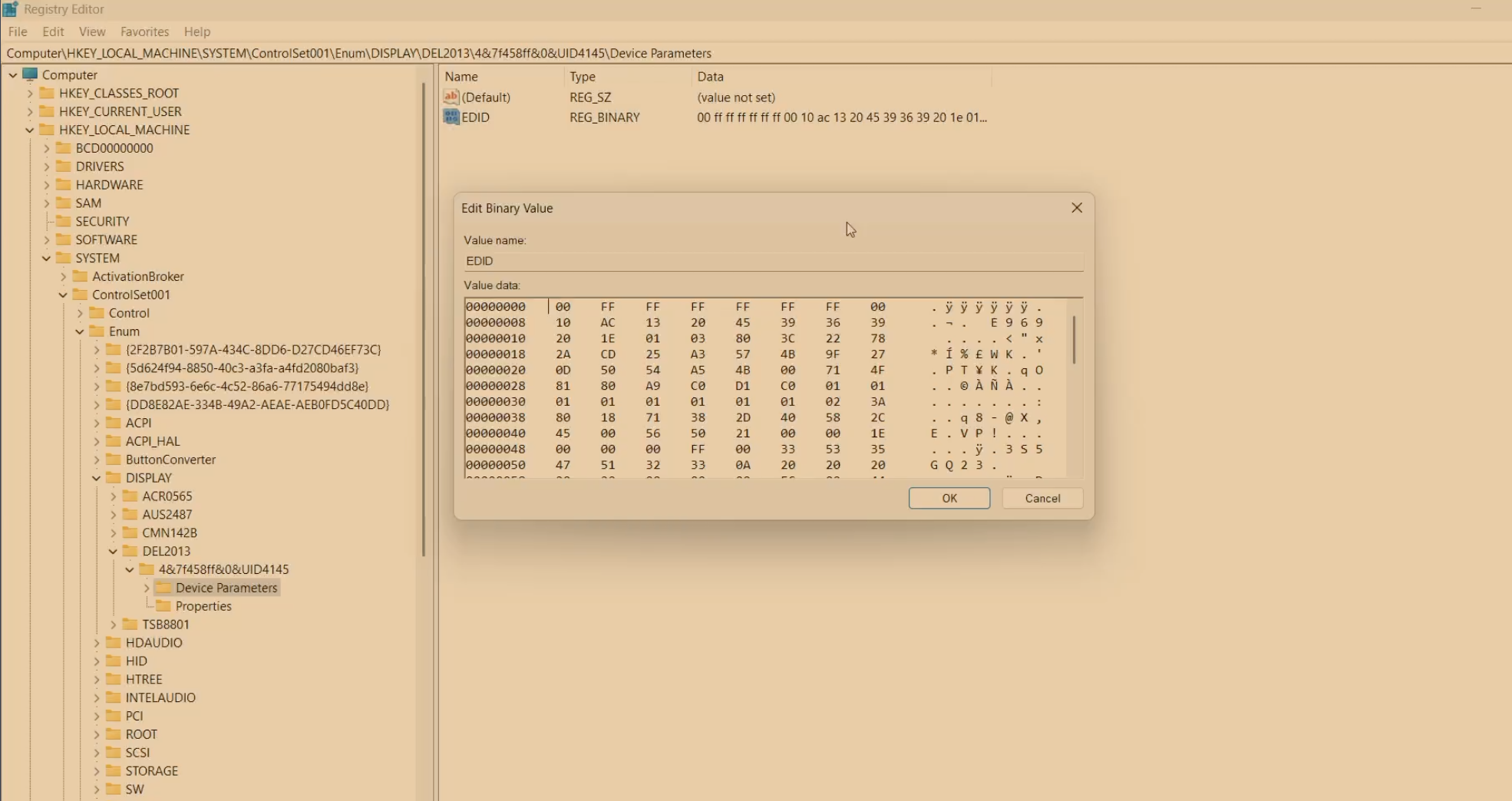
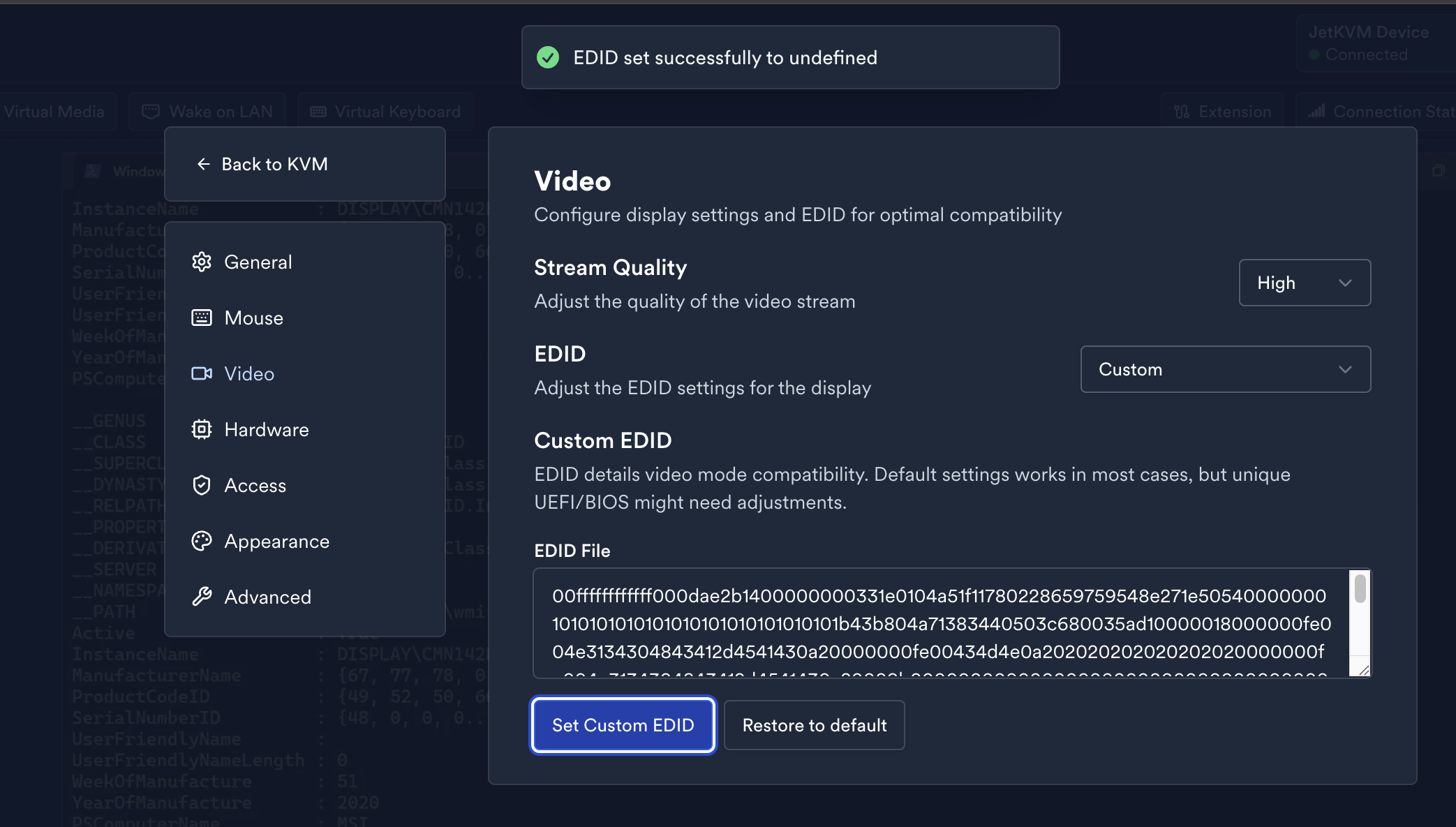
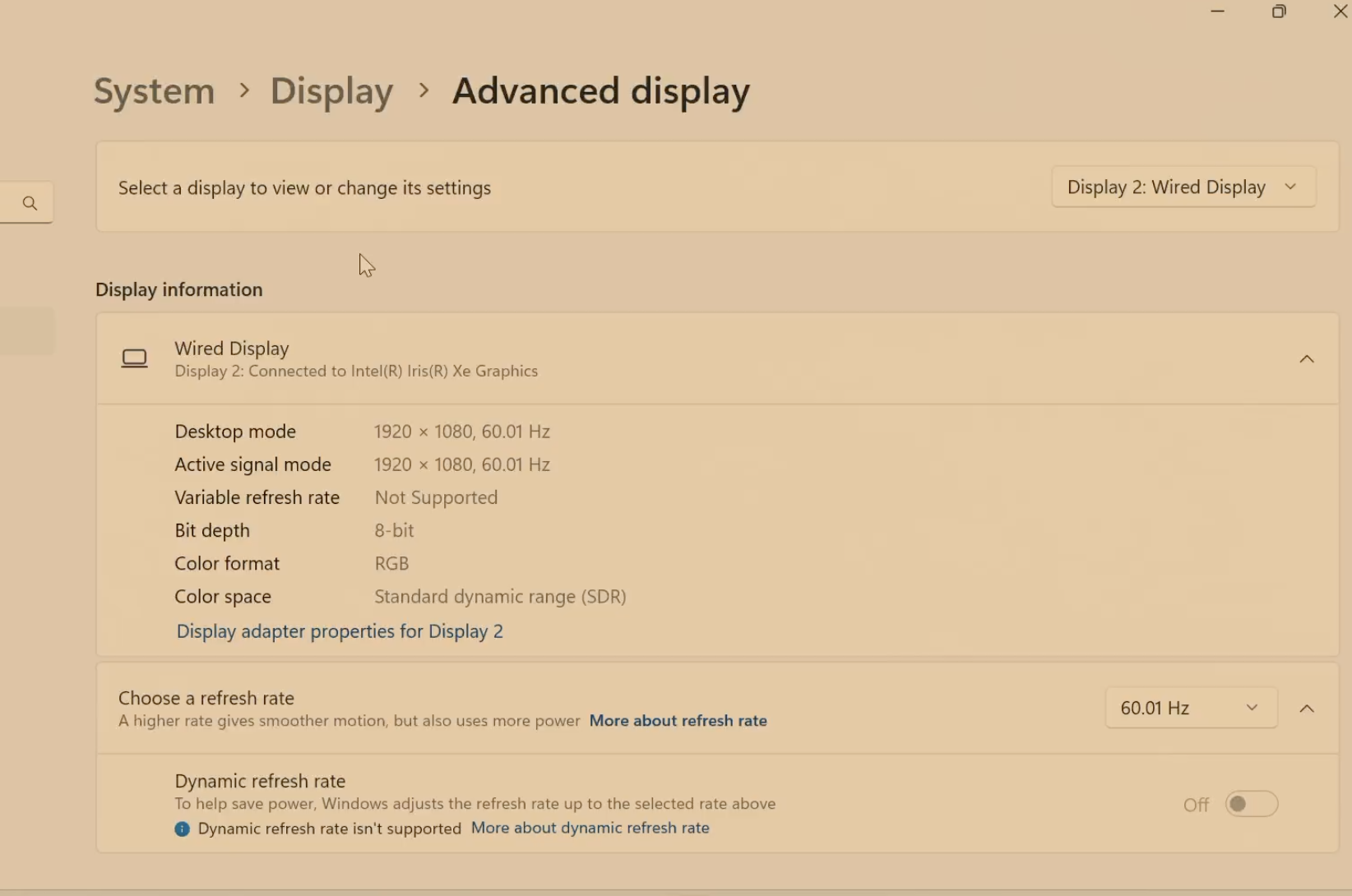
We took it a step further: by extracting and decoding the EDID (Extended Display Identification Data) from the host machine’s built-in display, converting it to hex, and uploading it to the JetKVM dashboard, we made JetKVM perfectly mimic the original display.
The system recognized it as the exact same built-in monitor, with matching name, serial number, vendor ID, and other attributes — making forensic differentiation nearly impossible.
Furthermore we tried to get the EDID of the built-in display and mimic and it perfectly worked out!!! as shwon in the screenshots below.![]()
![]()
![]() —
—
The Forensic Blind Spot
- Registry Traces: Spoofed vendor IDs can only be found under
HKLM\SYSTEM\CurrentControlSet\Enum\USB— and even then, they can be made to look legitimate. - Network Red Flags:
No traceon the system as it connects with seperate LAN - Physical Evasion: The device is tiny and easily hides behind monitor cables or docks.
The Bigger Picture
This isn’t just about JetKVM-hardware-based threats are evolving. Think:
Offline data theft via rogue charging stations.
Supply chain attacks with pre-installed KVMs in “new” hardware.
⚠️ Call to Action:
- Share detection strategies-comment below if you’ve tackled similar threats!
🛡️ Special Thanks
This research wouldn’t have been possible without the amazing support of my friend Akhil Dara

 The Invisible Insider!
The Invisible Insider!

 Amcache:The Most Misunderstood Artifact
Amcache:The Most Misunderstood Artifact LNK File Forensics — Experimental Case Study
LNK File Forensics — Experimental Case Study